CipherDecoder.org is a comprehensive online platform offering a wide array of cryptography tools for encoding, decoding, and analyzing various ciphers. It serves as an invaluable resource for students, educators, developers, and anyone interested in understanding the fundamentals of encryption, from ancient methods to modern encodings.
Key Features
Extensive Cipher Collection: Supports classic substitution ciphers (Caesar, Atbash, ROT13, Affine, Vigenère, Playfair) and transposition ciphers (Rail Fence, Columnar, Route, Scytale).
Modern Encoding & Tools: Includes Base64, Hexadecimal, Binary, URL Encoding, Morse Code conversion, ASCII Converter, and Hash Generator (MD5, SHA-1, SHA-256).
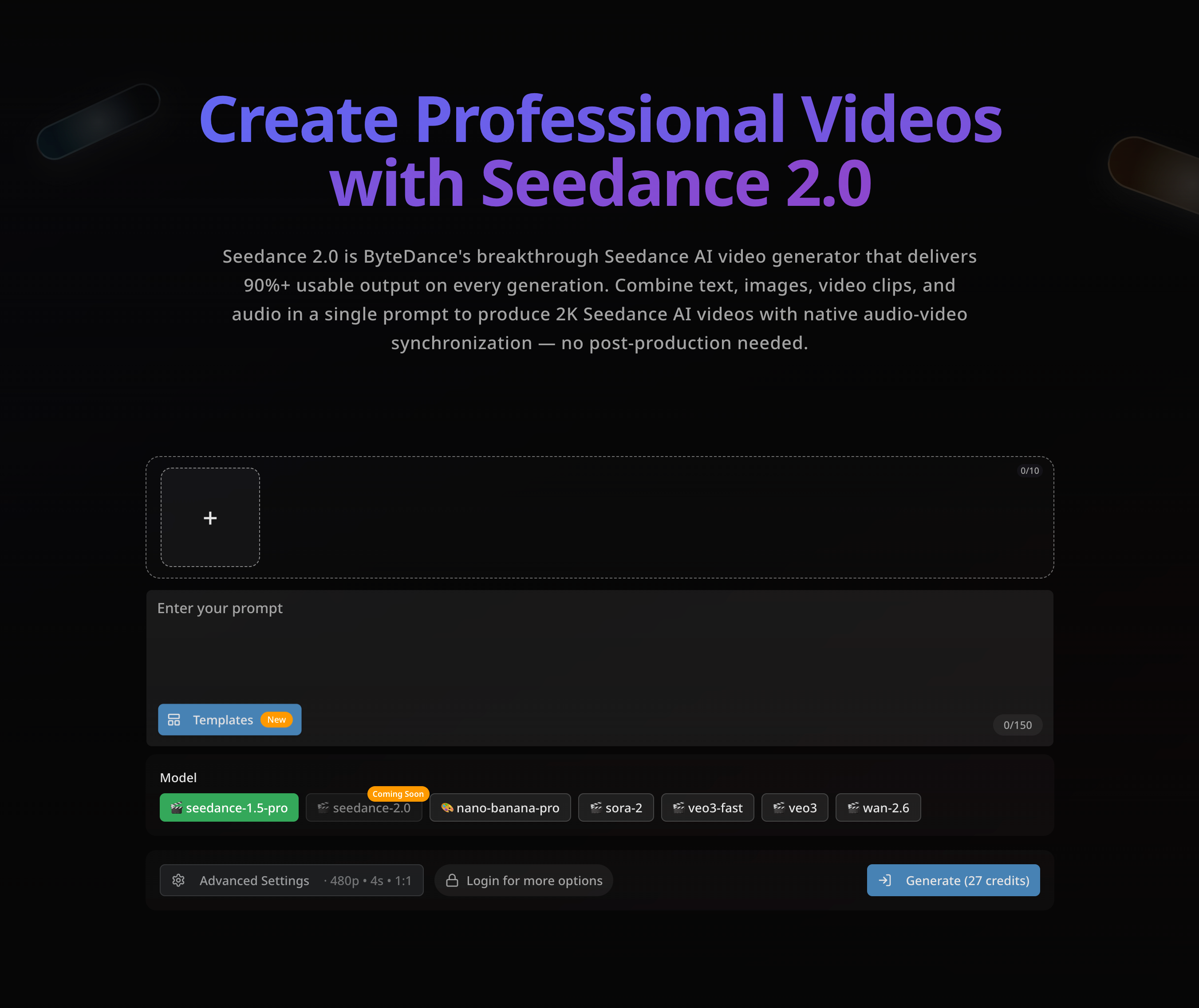
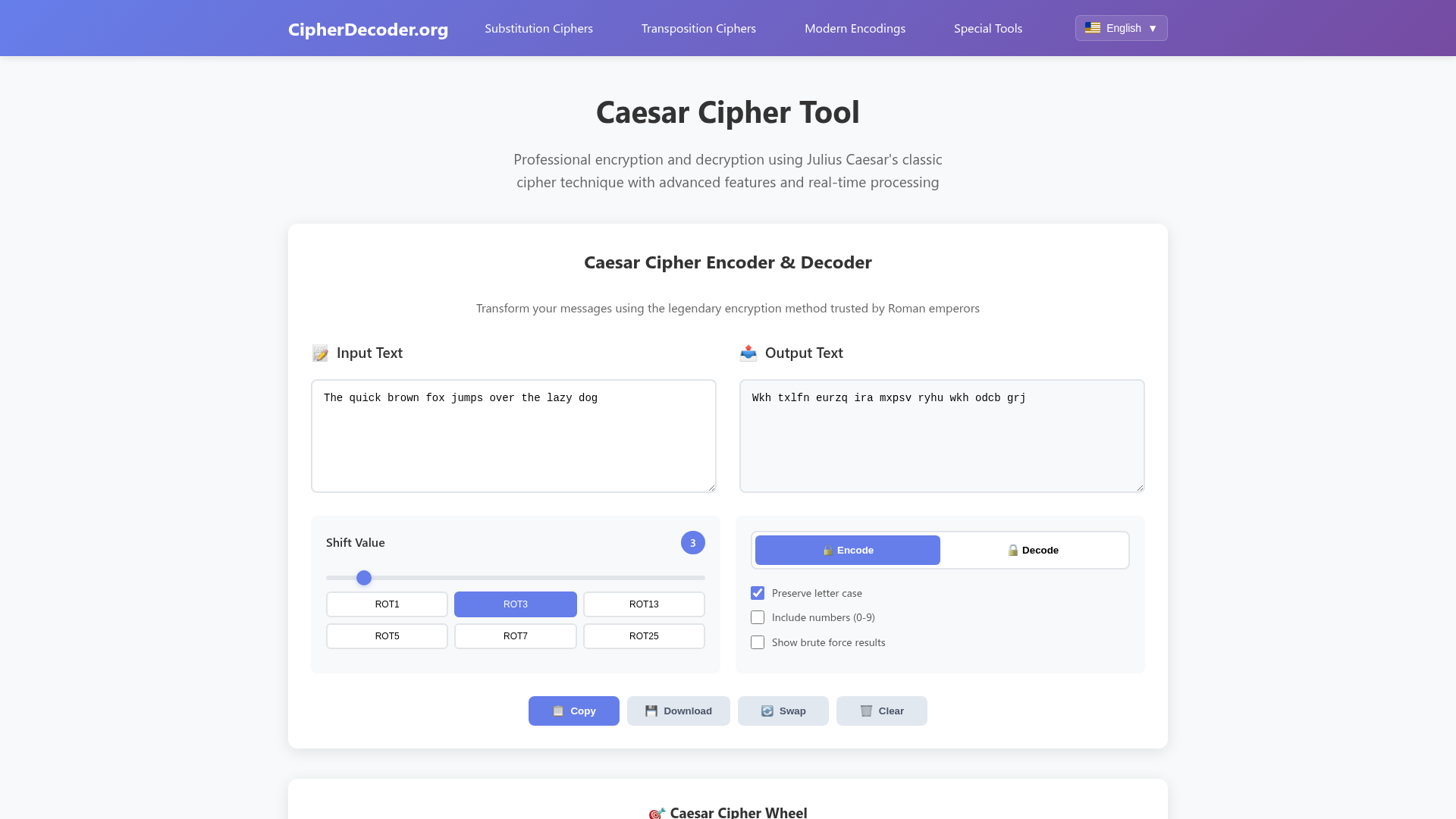
Real-time Caesar Cipher Tool: Professional encryption and decryption with advanced options like preserving letter case, including numbers, and showing brute force results.
Multi-language Text Analysis: Offers frequency analysis for English, Chinese, Spanish, French, German, Japanese, Arabic, Portuguese, Russian, Korean, and Hindi.
Educational Resources: Provides historical context, security analysis, and explanations of cryptographic principles.
Use Cases
CipherDecoder.org is ideal for educational settings, serving as a hands-on tool for students to learn about cryptographic principles, symmetric encryption, and cryptanalysis. It helps in understanding concepts like pattern recognition and mathematical thinking through practical application. Developers can use it for quick text obfuscation, testing basic encryption logic, or as a component in programming challenges.
Beyond education, the platform is useful for creating puzzles, online challenges, or simply for curious individuals wanting to explore the mechanics of various ciphers. Its ROT13 variant is particularly popular for hiding spoilers in online forums, demonstrating a simple yet effective real-world application of a Caesar cipher.
Pricing Information
CipherDecoder.org is a completely free online tool, providing full access to all its features without any cost. There are no hidden fees, subscriptions, or premium tiers, making it an accessible resource for everyone.
User Experience and Support
The platform boasts a professional and intuitive user interface, designed for ease of use with real-time processing for many of its tools, such as the Caesar Cipher Encoder & Decoder. Users can quickly input text and see immediate output. Comprehensive support is available through an extensive FAQ section, a cryptography guide, and educational materials that explain the historical legacy, mechanism, mathematical foundation, and security analysis of various ciphers.
Technical Details
While specific programming languages or frameworks are not explicitly mentioned, CipherDecoder.org operates as a web-based application, leveraging modern web technologies to provide its real-time encryption, decryption, and analysis capabilities directly through a browser interface.
Pros and Cons
Pros:
Comprehensive suite of classic and modern cryptographic tools.
Excellent educational resource with historical context and explanations.
User-friendly interface with real-time processing.
Supports multi-language frequency analysis.
Completely free to use.
Includes modern encoding and utility tools.
Cons:
Classic ciphers (like Caesar) are not secure for sensitive modern data.
No explicit API for programmatic integration (though API documentation is mentioned as a resource, it's not a core feature of the *tool* itself).
Limited information on advanced customization options.
Conclusion
CipherDecoder.org stands out as a robust and accessible online platform for exploring the fascinating world of cryptography. Whether for academic learning, practical application, or simple curiosity, it offers a rich set of tools and resources. We encourage you to visit CipherDecoder.org and unlock the secrets of ciphers today.